Device safety
- Devices are types of technology that usually connect to the internet, such as a smartphone, tablet, or computer
- There are always some risks to privacy and personal information when using technology. You always leave a digital trail so it may be important to use a safer device
- Safer devices are things like phones or computers that a person who has been abusive or violent has not and will not be able to access
- There may be more risks to your privacy and safety if someone who has been abusive or violent has had physical access the device you are using
- This site has general information about technology and safety. If you need more advanced specialist support for technology-facilitated abuse, please see the links at the bottom of the page
- Technology is always changing but the more you learn, the easier it will be to use
- You may want to ask a trusted person to help you with some of the suggestions on these pages.
- For support, you can call 1800RESPECT on 1800 737 732, text 0458 737 732 or visit our website for online chat and video call services:
- Available 24/7: Call, text or online chat
- Mon-Fri, 9am-5pm AEST (except national public holidays): Video call (no appointment needed)
Devices and safety
A person whose behaviour is violent or abusive may use technology to harass, watch, control, or harm you. This type of abuse is called technology-facilitated abuse. It may be hard to know if you are being monitored with technology.
There are many types of technology-facilitated abuse, but most abuse tends to occur using devices and online accounts. This page covers devices. The previous page covers online accounts.
Using technology can make our lives easier. When someone is keeping you from being able to access technology, it can make daily tasks much harder and can isolate you from other people and information that you need.
Some signs of abuse using a device
Someone who is abusive or violent may try to control you through your device by doing things like:
- Breaking it
- Taking it from you
- Cutting off or controlling your mobile service
- Monitoring what you do on your device
- Cutting off or controlling your data limit
- Sending your colleagues, friends or other people messages from your account without your consent, with the aim of ruining your reputation or your relationships
- Changing your device’s settings so that your device is less private and secure or harder for you to use
- Threatening or posting private things from your device online
- Impersonating you to get private information about you from others
- Installing spyware or stalkerware onto your device.
Abuse is never your fault. Learning about your choices and technology may help you feel more in control of your life.
Think safety before making changes to your device
We recommend making a safety plan and getting support before making changes to your device or online accounts in case it could be unsafe for you. Trust yourself. You know your situation the best.
Everyone has a right to privacy and safety. However, changing your device settings to try to take back control from someone who has been abusive or violent could be unsafe.
Some people that are being monitored choose to get rid of an old device and/or use a new device to have private conversations. Creating brand new accounts that do not connect with old accounts may help you stay safer, too. If you can control and get into your accounts and devices it can help you stay in touch with the people and information that is important to you.
Someone who is abusive or violent may try to control you through your device by doing things like breaking it, taking it from you, or cutting off or controlling your mobile service.
Types of devices
The most common devices are smartphones, computers, and tablets. But any device that connects to the internet, or “the Cloud,” may have the ability to learn and share information about you.
Some examples of other devices that may be able to connect to the internet are:
- Health trackers
- Smart appliances, lightbulbs and temperature controls
- Smart home virtual assistants
- Toys and entertainment systems
- Newer cars
- GPS (location) trackers
- Smart assistive technologies and environmental aids
- Cameras and voice recorders.
These types of devices that can collect and share information over the internet are a part of the “Internet of Things.” Any device or online account that a person who is abusive or violent has had access to might be less private or secure.
Types of device settings and what they do
Your devices will generally have privacy, security, accessibility, and location settings. You can learn about these settings now and change them when it is safe for you.
Some smart home devices that connect to the internet, such as smart plugs, are controlled through another device, like a smartphone. Similarly, location trackers can be placed on your vehicle or belongings to give someone abusing you information on their device about where you are going.
Other types of devices, such as environmental controls used by people with disabilities, have settings that can be modified using a person’s pressure, breath, or eyebrow movement.
Changing settings on devices can help make your information more private and secure.
However, devices are only one part of technology safety.
Keep in mind that each app or online account may have its own privacy, security, accessibility, and location settings, too. We talk about how to secure your online accounts on the previous page.
Accessible technology and safety
Smartphones, tablets and computers
Smartphones, tablets, and computers make more things possible and supports people with disabilities. These devices connect to the internet, and most have a touch screen.
Settings and apps can be changed or added to help you do things like:
- Use the device even if it is difficult to touch the screen or a keyboard
- Connect adaptive accessories, such as hearing aids and switches
- Use RTT / TTY (real-time text / tele-typewriter) to communicate
- Control smart home devices such as lighting, temperature, doorbells, TVs, and locks
- Adjust screen settings to make things easier to see
- Know where ramps, elevators, accessible toilets and exits are located
- Control money and accounts
- Stay in touch with others by using things like video relay service (VRS), social media, texting, video chat, email and “walkie-talkie” style voice recording apps.
A person whose behaviour is violent or abusive may use technology to harass, watch, control, or harm you.
This type of abuse is called technology-facilitated abuse, and it can happen to people with a disability. The abuse is never your fault. The other technology and safety pages on this website have information that may be important to you.
We recommend making a safety plan and getting support before making changes to your device or online accounts in case it could be unsafe for you. Trust yourself. You know your situation the best.
How to get help with your devices
Technology is always changing, and a good way to learn how to change privacy, security, accessibility, and location settings on your devices is to search online. One way to figure out what to search for is to ask a question that makes you curious.
You can search on Google or YouTube to learn how to do things like:
- Limit what apps can see the contacts you have stored on your device
- Turn off or limit location tracking on your whole device or just in certain apps
- Lock your device using a security PIN, pattern, fingerprint or face recognition.
Try adding the make and model of your device in your search to get the most accurate information.
Here are some ideas for things you could type in a search:
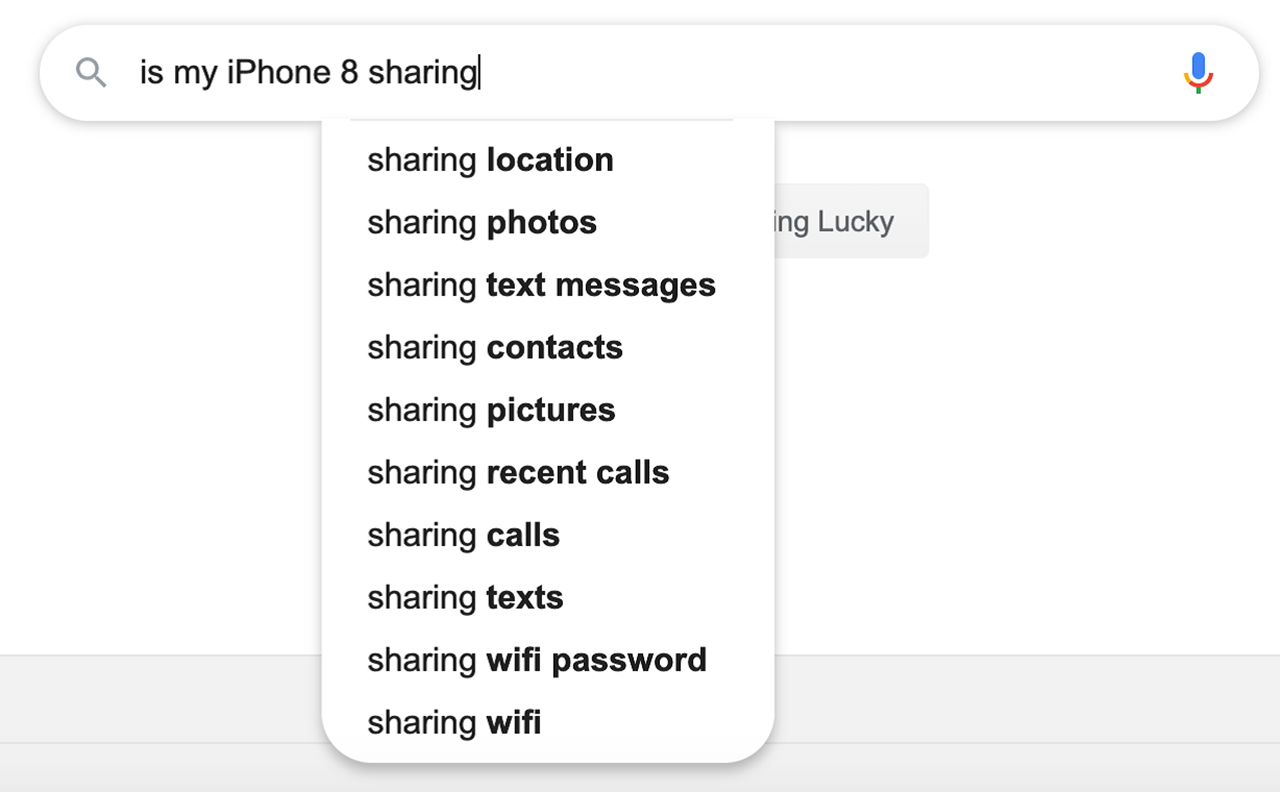
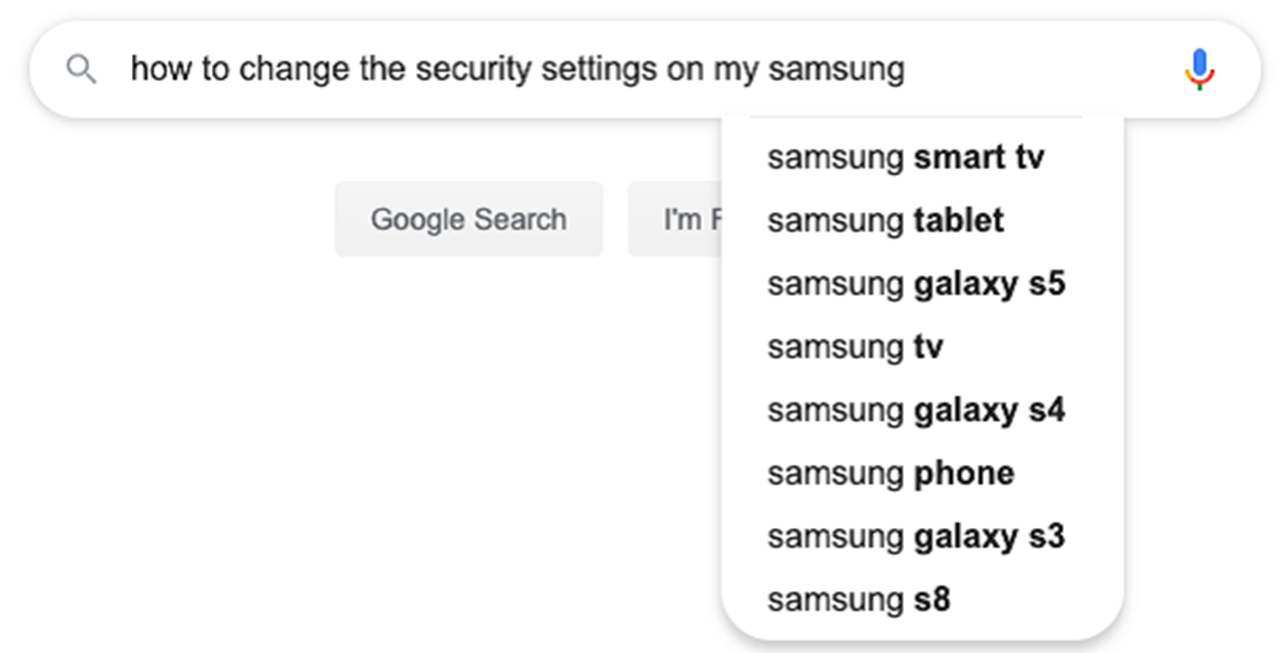
Once you start typing, most search engines will give you ideas based on their most popular searches.
Devices at risk of spyware and stalkerware
Spyware and stalkerware are types of programs or apps that can be put on devices that connect to the internet, usually without you knowing. They send your private information to another person.
Spyware and stalkerware can show someone what you do on your device even when they are not with you. This can include things like emails, texts, pictures, your location, your conversations and even what your device’s camera or microphone sees or hears.
Spyware and stalkerware can be a risk to anyone whose device has been accessed by someone who is abusive.
What you can do if you have spyware or stalkerware on your device
Spyware is hard to find and often hides on a device so that you cannot see it. Stalkerware is usually disguised as another type of useful app such as a parental monitoring app or an anti-theft app.
Some people that suspect spyware or stalkerware keep using their device normally, but they may also use a safer device to share information they want to keep private.
It is important to trust your instincts. If you sense that you are being monitored, the bottom of this page lists places where you can get specialised help with technology-facilitated abuse.
A safety check-up for devices
Here are a few tips to keeping yourself and your devices safer:
- Install regular software updates immediately
- Keep your devices charged. Hide a spare phone, charger, or power bank for emergencies
- Do not leave your device with anyone else, even for a short time
- Set your devices to lock immediately after use
- Think about the benefits and risks of transferring data from an old device to a new device
- Learn about what information is stored on your device and and whether or not it is also backed-up and stored online (usually through a cloud storage app like iCloud or OneDrive). You can change the settings in your device to store only what you want to in the Cloud.
Get more detailed advice about technology safety
WESNET
The Women’s Technology Safety & Privacy Toolkit is a resource from the Safety Net Australia Project at WESNET that was designed specifically for women experiencing technology-facilitated abuse. This toolkit includes guides ranging from online privacy and safety tips to smartphone privacy, location safety information, and much more.
eSafety
WomeneSafetyWomen has a range of resources, guides and videos to support safer use of technology. As well as covering things like general device and online safety, there is also information on how to be safer when using websites like online banking or online dating.


